API security
What is API security?
Application program interface (API) security refers to policies and procedures that protect APIs against malicious attacks and vulnerabilities.
Because APIs are key to programming web-based interactions, they've become a target for hackers. As a result, basic authentication requiring only user names and passwords has been replaced with various forms of security tokens, such as those used by multifactor authentication (MFA) and API gateways.
What is an API?
An API is code that lets two software components communicate and share data. For instance, a weather app on a smartphone uses an API to get daily weather information from a service. To provide weather updates to the user, a phone's weather app talks to this system via APIs. Another example is using a social networking app to send or receive messages. Social media platforms such as Facebook, Twitter and Instagram all provide APIs for developers to use in their apps. These APIs connect users when they send and receive messages using these apps.
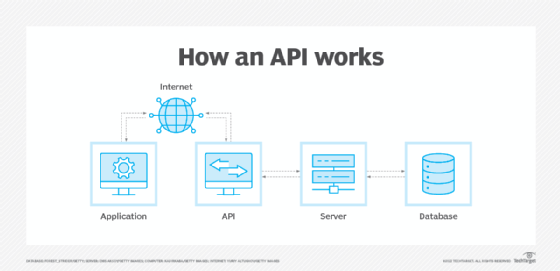
APIs are constructed using either Representational State Transfer (REST), an architectural style for developing web services popular due to its simplicity, or Simple Object Access Protocol (SOAP), a message protocol that lets distributed elements of an application communicate.
SOAP can be carried over a variety of lower-level protocols, including the web-related Hypertext Transfer Protocol (HTTP). REST APIs use HTTP; Transport Layer Security (TLS); and JavaScript Object Notation, a text-based, human-readable data interchange format used for representing simple data structures and objects in web browser-based code.
Importance of API security
Due to the rise of the internet of things, microservices and serverless architectures where most apps depend on APIs for core functionalities, cyber attacks are becoming more common. According to Salt Security, 94% of organizations experienced security problems in production APIs in 2022, and one in five suffered a data breach due to security gaps in APIs.
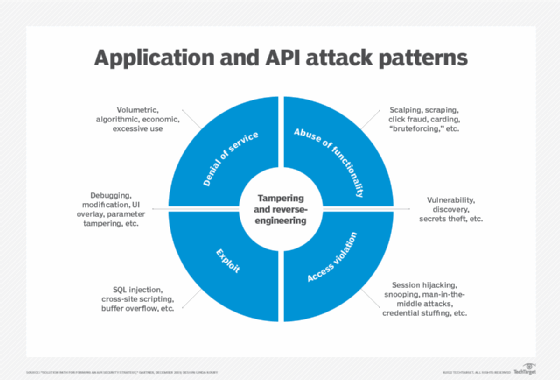
The non-profit organization Open Web Application Security Project (OWASP) also listed the potential security risks associated with APIs in its "Critical OWASP Top 10 API Security Threats" list. Attacks that could be inflicted on APIs include man-in-the-middle attacks, parameter attacks, SQL injections, distributed denial of service attacks and identity attacks. OWASP is set to release its latest version of the API Security Top 10 list later this year.
As a result, many of the largest web service providers are requiring partners to increase security and incident response measures, including the use of MFA, a security system that requires more than one method of user authentication from independent categories of credentials to verify the user's identity for a login or other transaction. Such service providers include Amazon and Microsoft, the latter which in August 2019 began requiring its cloud solution provider program partners, control panel vendors and advisor partners to enforce MFA for each user, including service accounts.
Adopting API security is important because it can prevent attacks, such as cross-site scripting (XSS) and SQL injections, as well as shield sensitive data from breaches. Overall, API security is vital to the successful and secure performance of APIs and the programs they support.
How does API security work?
While authentication and permission are the primary tools APIs use to function, they can be built with additional security to make them less susceptible to intrusions from outside sources.
The following are some features and functionality of API security:
- Authentication. API security relies heavily on authentication, as it's the first step that verifies the client application possesses a safe identity and is allowed to use the API.
- Authorization. Authorization is a subsequent step that involves determining what data and actions an authenticated application can access while interacting with the API.
- Reduction of vulnerability attacks. In addition to properly implementing a secure authentication and authorization system, APIs should be developed with other protective features to reduce the system's vulnerability to security threats during API calls.
- Collection of input. The API developer is responsible for ensuring their constructed API successfully validates all input from users collected during calls.
- Defense from attacks. Using prepared statements with bind variables is one of the most effective ways to shield an API from SQL injection. The language used to write the API frequently contains functionality that can assist in this security measure.
- Cleaning of the user input. XSS can be feasibly dealt with by cleaning the user input from the API call. By cleaning the input, Hypertext Markup Language and JavaScript tags are erased, and potential XSS vulnerabilities are minimized.
- Throttling. Throttling enables the management and limitation of a client's access to data. It measures irregularities in a client's use of the API and creates an extra layer of security between the client and sensitive information.
- Rate-limiting. Rate-limiting can mitigate denial of service (DoS) attacks on APIs. It entails limiting the number of requests that a user can make to an API at a time to reduce the attack surface.
- Log monitoring. API security also involves monitoring API logs for suspicious activity, including attempts at unauthorized access.
API security types and tools
The choice of an API security tool or measure must consider the needs of all entities involved in managing APIs, such as application security managers, developers and penetration testers.
The following are some common security systems and tools organizations use to protect APIs:
- Open Authorization. OAuth is an open standard for token-based authentication and authorization on the internet. OAuth enables third-party services to use an end user's account information, such as Facebook, without exposing the user's password. OAuth acts as an intermediary on behalf of the end user, providing the service with an access token that authorizes specific account information to be shared. The process for obtaining the token is called a flow.
- API managers. API managers oversee APIs in a secure, scalable environment. The goal of API management is to enable organizations that either publish or use an API to monitor the interface's lifecycle and ensure the needs of developers and applications using the API are being met.
- MFA. MFA is a security system that requires more than one method of authentication from independent categories of credentials to verify the user's identity for a login or other transaction.
- Transport Layer Security. TLS is a protocol that provides authentication, privacy and data integrity between two communicating computer applications. It's the most widely deployed security protocol used today for web browsers and other applications that require data to be securely exchanged over a network, such as web browsing sessions, file transfers, virtual private network connections, remote desktop sessions and voice over IP.
- Security Assertion Markup Language. SAML is an open standard for sharing security information about identity, authentication and authorization across different systems. SAML is implemented with the Extensible Markup Language (XML) standard for sharing data, and SAML provides a framework for implementing single sign-on and other federated identity systems.
Challenges of API security
API security poses the following challenges:
- Different from web applications. Since APIs operate and react in completely different ways than web applications, their security landscapes and infrastructures must be thought of in ways unique to their behavior.
- Security challenges with service APIs. Some cloud-based software as a service is only available through APIs known as service APIs. Service APIs create security challenges because they deal with data in high volumes and vary in security and authentication models.
- Unique applications. All applications are different, but to secure an API, the design must be understood. This involves reading and sorting through layers and variations of code that change based on technology and human differences.
- APIs can help attackers hide. APIs introduce new file formats, protocols and structures in their performance. These new and varied pieces make it easier for hackers to obscure well-known attacks, such as XSS or SQL injection.
- Internal APIs require protection. APIs can also be used internally or within the same system. This different use of APIs requires new security considerations and a possible overhaul of existing security infrastructure.
- Clogged pipelines. Developers and DevOps teams are responsible for providing security teams with information on what specific API endpoints do and how they operate. However, this information is frequently lost in cross-functioning communication, making it impossible for security teams to fully understand the API they’re working with.
- Accidental backend visibility. If not properly monitored and secured, APIs can mistakenly provide attackers with access to the backend functions of applications.
REST API security vs. SOAP API security
As mentioned earlier, there are two main types of APIs: SOAP APIs and REST APIs, or RESTful APIs. The following are the main features and differences between the two APIs:
- REST APIs are more modern while SOAP APIs have been around longer and are widely adopted.
- Both types of API display data with HTTP requests and responses. However, the formats and syntax they use to do so have major differences.
- Both APIs support secure sockets layer for data protection throughout the transfer process, but additional features differ between the two models. Therefore, security in SOAP versus REST APIs depends on the format and semantics used in each.
- Since SOAP APIs have been around longer than REST APIs, extensions have been added to SOAP that deal specifically with transactional messaging for certain security considerations.
- The use of SOAP in large enterprises lets the API benefit from World Wide Web Consortium and OASIS recommendations, specifically XML encryption, XML signature and SAML tokens.
- SOAP also offers superior support for web services specifications. The WS-ReliableMessaging specification provides SOAP with built-in communication error handling, and the WS-Security specification enables enterprise-level security protection. REST APIs don't include any specific security patterns or features. This is mainly because the API focuses on how to deliver and consume data rather than on how to build security and safety into the communication process. It shouldn't be assumed that their security measures come out of the box. Therefore, developers using REST architecture patterns, deployment and transmission must pay close attention to implementing security in code.
- While WS-ReliableMessaging provides built-in error handling for SOAP APIs, REST APIs must resend the data whenever an error occurs.
- If sensitive data is being managed, such as bank accounts and credit records, then SOAP might make the most sense when choosing an API model. However, the true strength of API security depends on how the API is implemented. A REST API that has been securely constructed and implemented is safer than a poorly designed and implemented SOAP API.
API security best practices
To guarantee API security and safeguard enterprises against potential attacks, an organization should implement the following API security best practices:
- Authenticate and authorize. API queries should always be authenticated and authorized to guarantee that the user making the request is who they claim to be and has the proper permissions.
- Use a gateway. An API gateway should be used to manage and secure API traffic, as it provides authentication, routing, rate restriction and other security capabilities. Therefore, APIs should be kept behind a firewall, web application firewall or an API gateway.
- Encrypt API requests and responses. TLS encryption should always be used to protect the security of API requests and responses.
- Validate API requests. All API requests should be validated to ensure the data is correctly formatted and conforms to the expected schema. This can help mitigate injection attacks and other security vulnerabilities.
- Implement access control. Access control should be used to ensure that users don't have access to all resources but only the ones that they require access to.
- Use scope for coarse-grained access control. Scopes should be used to restrict each access token to a certain group of resources.
- Store API keys securely. API keys should be kept private and they should never be included in API requests to prevent them from getting stolen. Threat actors can easily exploit stolen API keys to access sensitive information.
- Rate limit API queries. API queries should be rate regulated to prevent DoS attacks and other security vulnerabilities.
- Keep APIs current. APIs should be updated with the most recent security fixes and updates to guarantee they remain secure over time.
APIs are a prime target for hackers, as they represent the foundation of modern application design. Read this guide to learn how to defend APIs from threats and other security vulnerabilities.







